EXECUTIVE SUMMARY:
In cyber security, the available potential workforce isn’t keeping pace with demand. In the U.S., more than 750,000 cyber security positions remain unfilled, and globally, more than 3.5 million cyber security job vacancies exist.
“While Amazon, Meta, Twitter, Microsoft, Google and other tech giants are going through layoffs, our industry has hung out an enormous ‘Help Wanted’ sign,” says Steve Morgan, founder of media group Cybersecurity Ventures.
However, despite the ‘help wanted’ signs, the talent gap hasn’t yet been resolved. As a result, some CISOs are redesigning staffing plans in order to address challenges associated with recruiting, hiring and retaining security professionals.
In this article, discover the talent-to-value framework. See how it can enrich hiring practices and increase staffing while reducing your cyber security risk.
What is the talent-to-value framework?
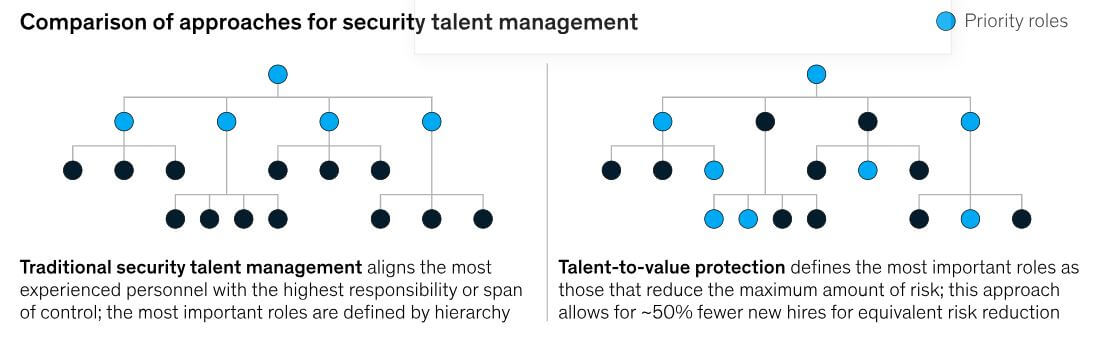
In the talent-to-value framework, leaders clearly define the most important cyber security roles — the ones that yield the greatest reduction in risk for the enterprise.
When hiring, most leaders use a top-down approach that involves filling the highest level roles before filling roles further down the organizational chart. However, due to the worker shortages, and high (sometimes exorbitant) costs associated with competitive talent, the standard hiring approach is not-so-effective in this job market.
The daunting threat landscape means that organizations may need to manage cyber security talent more flexibly than for other departments. By gaining a holistic picture of an organization’s cyber security needs, leaders can create a hiring roadmap that hones in on the most critical security initiatives and roles. And those roles aren’t necessarily going to be at the very top of the org chart, as might be expected.
Talent-to-value in action
In the talent-to-value framework, the most important roles are the ones that lead to maximal risk reduction; the ones that result in the highest levels of security value.
Talent-to-value allows for reduced risk through focused hiring and talent development. The approach assists with identification of skills and roles are the highest priority when it comes to risk management. In other words, the approach allows for clear understanding of the roles that demonstrate the greatest “return on risk investment.”
In short, the talent-to-value framework enables organizations to hire the right people at the right time. It ensures that near-term cyber security hiring is aligned with business growth objectives.
Assumption-based hiring
Less mature firms often believe that they need to hire based on cyber roles, regardless of the specific cyber security risks inherent in their industry or organization. As noted previously, the talent-to-value framework emphasizes the importance of hiring the right individuals at the right time. Via talent-to-value, leaders can better evaluate where to apply resources to best reduce risk.
The three-step approach
Integrating the talent-to-value framework into an organization is a three step process. Brief descriptions of each step are provided, below. In applying the talent-to-value framework:
1. First, identify prioritized tasks. Through risk modeling and the assignment of scores to potential vulnerabilities based on risk, the talent-to-value framework asks leaders to map out a set of cyber security tasks that are top priorities when it comes to executing on a cyber security strategy. Although every organization will assign risk scores differently, scores should be based on the business or operational impact of weakness exploitation.
2. Second, define which roles will lead to maximum risk reduction. The next step is to define and prioritize security roles required to account for the top risk-based priorities. After priority roles are defined, leaders can create job descriptions pertaining to what the organization needs within each role.
3. Determine whether priority roles can be filled by upskilling existing talent or whether hiring new talent is truly needed. Once job descriptions for priority roles have been created, leaders can analyze who, if anyone, in their current teams could be suitable for the roles. In some instances, it is more efficient and less expensive to upskill team members than it is to hire new personnel. And for some organizations, it may make sense to outsource talent in order to accelerate implementation and scale security support quickly.
Conclusion
The talent-to-value framework enables organizations to see what type of skills are really required for risk management, to clearly understand who they need to hire and to define expectations around risk reduction outcomes. Via the talent-to-value model, leaders may realize that they don’t need a cloud security manager — rather, they need a cloud security architect with specific types of experience.
Amidst the continued cyber security talent shortage, talent-to-value allows organizations to be more strategic in terms of who they hire, who they upskill, actual risk reduction and return on security investments.
For an expanded set of insights pertaining to the talent-to-value framework, please click here. If interested in more cyber security talent management strategies, please see CyberTalk.org’s eBook. Lastly, subscribe to the CyberTalk.org newsletter for executive-level interviews, analyses, reports and more each week. Subscribe here.




