EXECUTIVE SUMMARY:
A bug in a new endpoint system developed by Meta could have allowed a hacker to turn off an account’s two-factor authentication. In simpler terms, a hacker could have turned off the two-factor authentication on your Facebook account at any time prior to mid-September of 2022. A hacker just needed a phone number to make it happen.
Facebook findings
Last year, a security researcher observed that Meta had not set up login attempt limits following a user’s input of a two-factor code used to log into the new Meta Accounts Center, which is designed to help users connect all of their Meta accounts.
An attacker in possession of a victim’s phone number could visit the Meta Accounts Center, input the phone number of the victim, link the number to their own Facebook account, and then brute-force the two-factor text message code. The latter was the key step because there was no upper limit to the number of two-factor text code input attempts that a person could make.
After an attacker successfully brute-forced their way into the account, having cracked the authentication code, the victim’s phone number could be linked to the attacker’s own Facebook account. The Meta platform would then end up sending a message to the victim, saying that their two-factor authentication was disabled and that the account had been linked to a new profile.
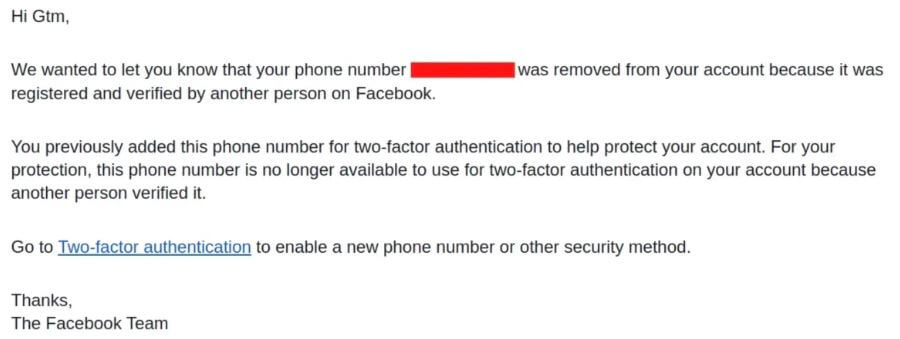
“Basically, the highest impact here was revoking anyone’s SMS-based 2FA just knowing the phone number,” said the security researcher who identified the flaw, Gtm Mänôz.
Facebook account takeover
The entire aforementioned process meant that two-factor authentication was no-longer enabled for a given account. At that point, a cyber attacker could attempt to take over the account simply by phishing for the password.
The bug was reported
Mänôz reported this bug to Meta in mid-September. Meta fixed the bug within several days, and Mänôz received $27,200 for his findings.
A Meta spokesperson says that at the time of the bug, the login system hadn’t been scaled properly – they remained at the stage of a small public test.
A subsequent investigation showed that there was no evidence of exploitation in the wild. Meta did not see a spike in usage of the affected feature, which would have signaled cyber criminal abuse.
For more cyber and social media insights, please see CyberTalk.org’s past coverage.
If your organization needs to strengthen its security strategy, be sure to attend Check Point’s upcoming CPX 360 event. Register here.
Lastly, to receive cutting-edge cyber security news, best practices and resources in your inbox each week, please sign up for the CyberTalk.org newsletter.




